 Professionals of all types use working models. Medical professionals use models to describe how a disease can be observed and differentiated, and mental health professionals have developed various models throughout the decades. A valid model can help characterize threats and consistently track them as they evolve. It can help you see both the big picture and contextualize the little stuff.
Professionals of all types use working models. Medical professionals use models to describe how a disease can be observed and differentiated, and mental health professionals have developed various models throughout the decades. A valid model can help characterize threats and consistently track them as they evolve. It can help you see both the big picture and contextualize the little stuff.
Cybersecurity professionals use models too. Cybersecurity pros use models to provide clarity, identify how to place security controls and most importantly profile how cyberattacks are perpetrated. It’s very important to understand what most cybersecurity pros call the hacker lifecycle.
Understanding the Hacker Lifecycle Using 3 Cybersecurity Models
If you’ve ever looked into a typical intrusion detection application like Snort, a security information and event management (SIEM) tool like Splunk or a cyber threat intelligence (CTI) feed like AlienVault OTX, you’ve likely seen references to one or more hacker lifecycles.
These are models for hacking. In fact, you can find references to these models in thousands of applications. Artificial intelligence (AI) implementations, for example, often center around these models. That said, it’s a good idea to get to know them well.
The following models are core to understanding CTI, which is authoritatively defined by Sergio Caltagirone’s whitepaper Industrial Control Threat Intelligence.
Let’s take a look at the big three cybersecurity models used to investigate intrusions:
Lockheed Martin Cyber Kill Chain
This time-honored model has been around the longest, and cybersecurity pros and software applications refer to it often. Originally published in 2011, the Cyber Kill Chain, shown below, outlines seven steps that an attacker takes during an intrusion:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control
- Actions on Objectives
It is an effective model because it authoritatively lays out the typical steps an attacker takes. Furthermore, this model took the anecdotal wisdom of thousands of subject-matter experts and standardized a great deal of the vocabulary used in the industry.
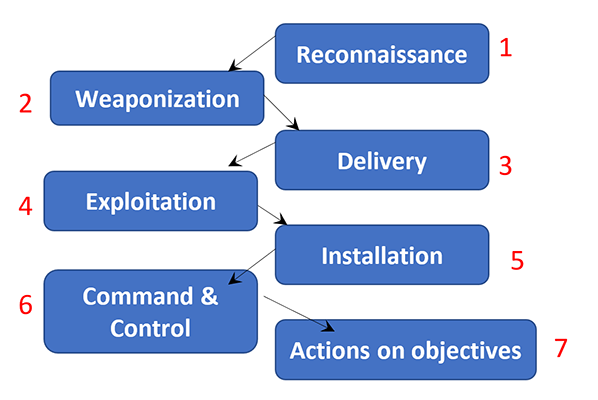
Figure 1: The Lockheed-Martin Cyber Kill Chain
The Lockheed Martin Cyber Kill Chain is quite linear in its approach, which can be a benefit. Cybersecurity professionals often find themselves in a “fog of more” situation. The ability to drill down to a specific step is often welcome.
However, this linearity can also be a problem because it may cause cybersecurity professionals to oversimplify situations or draw quick conclusions. Read more about the Lockheed Martin Cyber Kill Chain.
The Diamond Model of Intrusion Analysis
Sergio Caltagirone, Andrew Pendergrast and Christopher Betz felt that linear cybersecurity intrusion models had a few weaknesses. They wished to focus on specific hacker behaviors and create a model that allowed cybersecurity professionals to identify the relationships between attacker motivations, the victim and the technology used to wage an attack.
They first articulated the diamond model in 2006 and later published it in 2013. With this model, each event, such as an intrusion, is represented by a diamond.
Like a diamond, an event has four quadrants, and each quadrant describes core features:
- Adversary: The persona of the individual or group attacking you
- Infrastructure: IP addresses, domain names or email addresses
- Capabilities: What the adversary can do (e.g., malware, exploits, manipulate infrastructure)
- Victim: Can include people, services, network assets or information
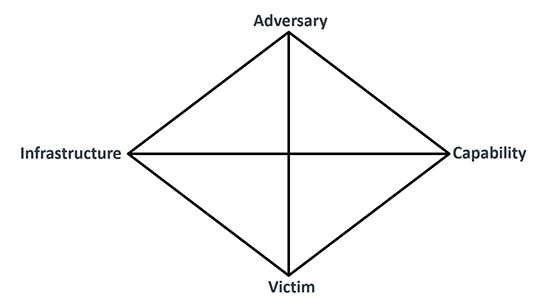
Figure 2: The four features in the Diamond Model: adversary, infrastructure, capabilities and victim
The idea behind this model is to get very granular concerning the relationship between the adversary (hacker) and the victim. Most importantly, the creators of the Diamond Model wanted ways to identify the activity of pivoting.
Pivoting Example
Remember when Luke Skywalker and the rest of the Rebels attacked the Death Star in Star Wars Episode IV? They identified and attacked a thermal exhaust port that was only two meters wide but led directly to the Death Star’s reactor.
The attackers made a lot of noise in their attack. If the Empire had responded faster – if they had pivoted their own defenses – the Rebel Alliance would have failed.
When a hacker pivots, they identify ways to attack a particular environment that is defended the least. Pivots can make a lot of noise – and the hope has been that the Diamond Model allows humans and machines alike to identify and evaluate that noise to determine intention.
Identifying hacker pivot points is difficult, but not impossible – as long as you focus on relationships between the adversary, the infrastructure, the capability and the victim.
The primary benefit of the Diamond Model is that it allows people – and AI applications – to identify when a hacker pivots. It also allows the cybersecurity analyst to do something called analytics pivoting, which is where the analyst identifies the relationship between attack techniques. The emphasis is less on the components themselves and more on the relationship between these components.
Using the Diamond Model, it is possible to string together multiple events – or diamonds – and create an activity group. This allows us to follow the steps of an attack throughout an entire hacker campaign.
One result of the Diamond Model is that it helped turn the activity of intrusion detection from an art into a science – where the activity can be taught and replicated. After all, if we want to move the IT talent needle, we’ve got to apply a bit of logic. Also, this model allowed software developers to apply AI to the activity of intrusion detection.
Attack Graphs: Combining the Cyber Kill Chain and the Diamond Model
The designers of the Diamond Model mapped it to the Cyber Kill Chain, calling them highly complementary of each other. Combining the two results in an attack graph, as shown below.
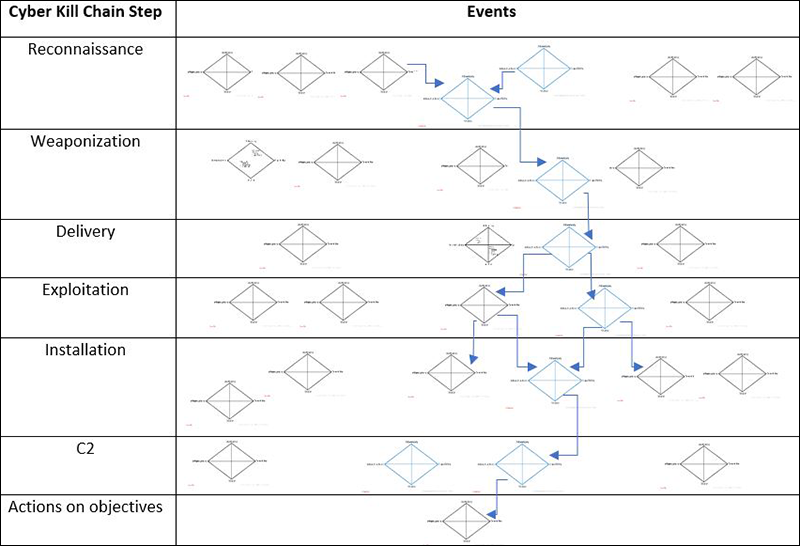
Figure 3: Viewing a series of unfortunate events – and pivot points – by combining the Cyber Kill Chain and the Diamond Model
The attack graph allows the cybersecurity analyst to identify not only each step of the Cyber Kill Chain, but also individual pivot points the hacker takes within those steps. The result is a far more rich and nuanced understanding of intrusion analysis, and this approach has formed the basis for most of the intrusion detection and SIEM tools that exist today.
The attack graph above shows a couple of pivot points: first in the Reconnaissance area and the second in the Installation section. The attacker appears to have considered a couple of different tactics but chose an area that could include a particular vulnerability (a low patch level), the exploitation of an installed tool (PowerShell) or a particular development environment (Python). The creators of the Diamond Model would argue that applying their approach to a linear model, such as the Cyber Kill Chain, allows software applications and defenders alike to gain a better understanding of an intrusion.
The MITRE ATT&CK Model
The Adversarial Tactics, Techniques and Common Knowledge (ATT&CK) model has become extremely popular over the past five years and is found in software applications everywhere. Many applications refer to it as the de facto standard for identifying steps of the hacker lifecycle.
According to the MITRE model, hackers take the following steps:
- Initial access
- Execution
- Persistence
- Privilege escalation
- Defense evasion
- Credential access
- Discovery
- Lateral movement
- Collection
- Command and control
Usually, MITRE places the steps hackers take in a larger context. For example, take a look at these steps listed in the MITRE ATT&CK Navigator, shown below.
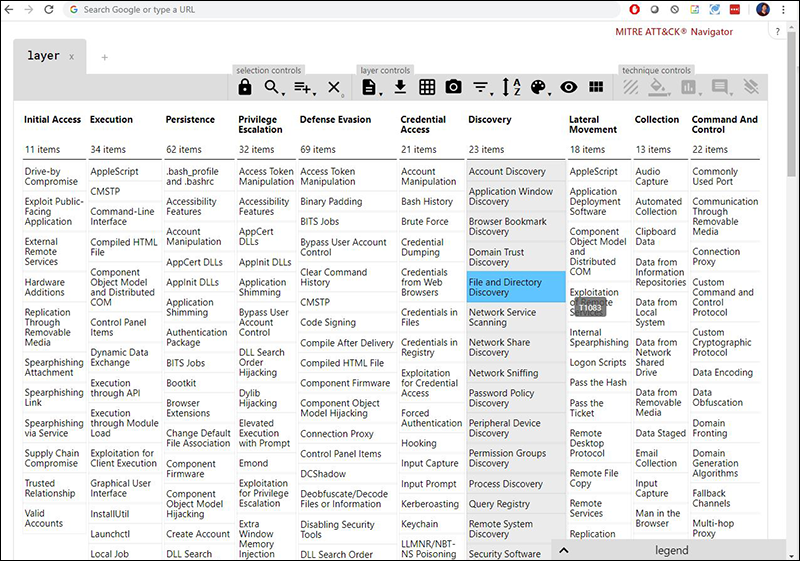
Figure 4: The MITRE ATT&CK Navigator
As you can see, the MITRE ATT&CK Navigator does more than just list a few steps. It maps specific tactics and procedures to each step. With the MITRE ATT&CK Navigator, you can map specific tactics and procedures to actual threat groups, identifying common techniques and procedures that attackers might take when they target your company.
For example, I’ve highlighted File and Directory Discovery as a possible procedure that an attacker might take. This way, I can begin to predict exactly how an attacker would do this, providing a valuable prevention strategy.
While it’s interesting to see how MITRE has mapped the idea of the hacker lifecycle to common technologies that potential victims use, it’s also interesting to see where MITRE makes slight changes to its particular hacker framework at various times.
For example, if you go to the MITRE ATT&CK Matrix for Enterprise, you’ll see a modified list of steps. I don’t see this as an inconsistency but as a need for customizing hacker models.
Selecting Cybersecurity Models to Meet Your Needs
No one model is better than the others. Cybersecurity professionals advise to choose your terminology – or model – and then stick with it. They also advise to add or modify a particular step to meet your needs. This advice isn’t contradictory, it simply means that no one model applies to all organizations. But, once you’ve made a few changes, use your terms consistently.
Think Like a Hacker to Stay Ahead of the Hacker
These three common hacker lifecycle models are not the only models. But, once you investigate them, you can then learn how to pivot in more sophisticated ways as a penetration tester or identify hacker pivots and strategies as a security analyst. The deeper you dig, the more you’ll discover. And the more you know, the better your defense will be against cyberattacks.
Show employers that you have the skills they need to identify cyber threats with the new CompTIA Cybersecurity Analyst (CySA+). Download the exam objectives for free to see what's covered.

