
What Is Cybersecurity?
Learn what cybersecurity is and understand the definitions of different types of threats.
 Ever curious why a word like malware sparks a not-so-warm-and-fuzzy feeling? We don’t typically feel so great about words like malevolent (for your favorite villains), malignant (for those unsavory human infections) or malicious
(getting closer to the IT world here) either. If you’re included in this group, you can rest easy knowing your instincts are sharp because malware is definitely NOT a good thing.
Ever curious why a word like malware sparks a not-so-warm-and-fuzzy feeling? We don’t typically feel so great about words like malevolent (for your favorite villains), malignant (for those unsavory human infections) or malicious
(getting closer to the IT world here) either. If you’re included in this group, you can rest easy knowing your instincts are sharp because malware is definitely NOT a good thing.
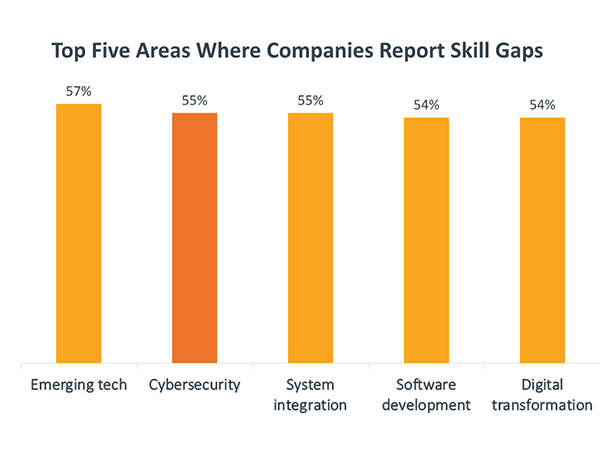
It’s important to know about malware because it’s one part of the big cybersecurity picture, and companies are hungry for IT pros with cybersecurity skills. In a recent survey that CompTIA fielded to several countries, cybersecurity ranked second behind emerging tech for skill gaps that companies were concerned about. Learning about malware and other cyberthreats is an important part of becoming a cybersecurity expert.
The word malware is a mash up of the words malicious and software. The term malware refers to any software that is intended to threaten or compromise information or systems. Hackers use malware to compromise networks or devices with the intent of stealing information or making a system inoperable. Malware is most often used to illicitly obtain information or disrupt business operations.
The first malware dates back to the 1980s. The first documented computer virus was discovered on a Mac in 1982 and was dubbed Elk Cloner. A strain of PC-based malware was discovered not long after in 1986 and was titled Brain.
The evolution of malware seems to directly correspond with the development of technology. Much like superheroes who develop new powers only to be met with an equally-matched enemy, malware often develops alongside the technology businesses are adopting. When email became popular, so did email-based malware, for example.
While it would be difficult to chronicle all the malware instances over the past 40 years, we can give you a brief rundown.
Types of Malware: Categories of Compromise Malware is a general term that encompasses many different types of threatening software. For IT pros, it’s important to identify which category malware falls into in order to determine the best approach for containment.
Here are the different types of malware:
This is by no means a complete list, but it offers a jumping-off point for identifying and evaluating more sophisticated threats.
Malware isn’t limited to PCs – it can invade mobile devices as well. As you may have guessed, mobile malware is a type of attack that targets the software specific to mobile devices. While attacks have traditionally targeted desktop computers, mobile malware is becoming more prevalent especially as mobile devices are utilized to conduct business affairs.
Mobile malware often mimics the types we see on larger systems and may include categories such as trojans, ransomware and spyware.
Android malware is software that specifically affects Android devices. In recent years, Google has identified malware that particularly affects Android devices and has caused a bit of chaos for Android users.
One especially nasty piece of Android malware, known as xHelper, was identified in April 2020. It uses a trojan to collect information from your device and then install another trojan. It gets so deep into your device that it may not be removable even if the device is reset to factory settings.
Similar to Android malware, iPhone, or iOS, malware is malware that specifically targets the software on iPhones and iPads. Given Apple’s stringent protocols, these devices are well-known for being largely impervious to malware. However, the popularity of these devices makes them a very appealing target, and they are not exempt from cyberattacks. For example, a zero-day vulnerability has recently been identified as a possible weakness to iPhones. The zero-day flaw created a vulnerability in Apple’s native mail app. Attackers could trigger the bugs by sending a large email to gain access to the target device.
Internet of Things (IoT) malware involves attacks of a different variety. Because IoT devices are by nature connected to each other, malicious attacks on IoT can potentially do large amounts of harm.
The connectivity between multiple systems and devices also makes it difficult to safeguard them with security software. One infamous IoT malware allowed hackers to control baby monitors, while still others targeted IP cameras and home routers. Read more about securing IoT devices, including baby monitors.
Protecting against malware is often easily done with responsible device and password management and a healthy dose of best practices.
Here are some tips to help protect your device and prevent malware:
Removing malware from your device can be tricky as there are so many different forms it can take. Here are some general steps you can take.
Android malware results from the download of a malicious app, and you can remove it in a way similar to how you’d resolve desktop-related issues. To remove Android malware from your device, shut down your phone and restart it in safe mode. If you still experience issues, try removing suspicious or unused apps. If all else fails, restore your factory settings. To prevent future Android malware, you can also install a mobile security app.
The iPhone remains one of the most secure devices because it does not use third-party app stores. Should you experience strange behavior from your iPhone, immediately restart your device. If that doesn’t immediately take care of any problems, clear your iPhone’s data and browser history. If all else fails, restore it to an earlier version.
Ransomware, malware, social engineering and phishing all encompass different forms of ill-intentioned cyberattacks.
While our guide acts as an introduction into the threats posed by malware, this is by no means an exhaustive list. Malware and the cybersecurity world change on a daily basis, and attacks are becoming increasingly sophisticated. The best way to combat cyberattacks is to stay informed about the latest attacks.
Read more about Cybersecurity.