While it often goes unnoticed by the average user, networks are implemented to isolate data from the outside world. Organizations rely on networking to connect their devices and integrate their systems across geographical barriers, while ensuring safe passage for information.
This quick-start guide walks you through the basics of setting up your cloud network. If you’re an IT pro with your sights set on designing and implementing a cloud network, join us on this brief tour.
Attraction 1: What Is a Virtual Network?
Virtual networks can be thought of as separate networks within a larger network. Administrators can create a separate network segment consisting of a range of subnets (or a single subnet) and control traffic that flows through the cloud network. Depending
on your business needs, you can implement your network using cloud technology from a cloud service provider (CSP).
The key difference for cloud administrators and architects when it comes to designing cloud networking solutions is the amount of control needed to have over the hardware. When you implement cloud networking with a CSP, you have little control over —
and likely little knowledge about — the design of the CSP’s network. Because of this limitation, virtual networks are often the go-to choice when you want to provide secure network isolation.
With a cloud solution, these virtual networks are known as VNets or Virtual Private Clouds (VPC). These act as a representation of a network in the cloud, giving you a cloud network.
Virtual networks provide the following benefits:
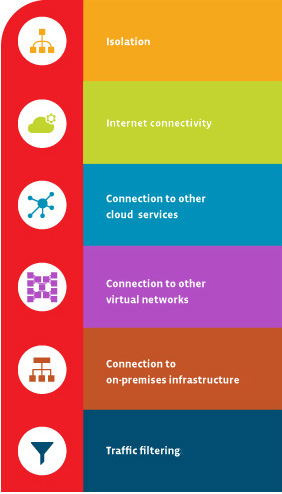
- Isolation
You can keep networks isolated from one another to ensure security and for purposes of development, quality assurance and deployment of cloud networks. - Internet Connectivity
Each virtual network can be configured to access or deny access to the internet, or to limit access to specific destinations on the internet if needed. - Connection to Other Cloud Services
Virtual networks often need a connection to CSP services. This allows the network to utilize services offered by the CSP. Providers typically allow for configuration of routing tables, domain
name resolution, firewall and related items to manage the connections to your virtual networks. - Connection to Other Virtual Networks
This allows you to interconnect your virtual networks when necessary while maintaining control over connections. - Connection to On-Premises Infrastructure
Part of the flexibility of a virtual network is the ability to control connections. You can connect your virtual network to on-premises systems. Often this type of configuration is for
end users to access a secure private cloud network or done as part of a hybrid cloud implementation. - Traffic Filtering
Most secure connections involve filtering. Normally, this involves filtering items by source IP address and port, destination IP address and port, and particular protocol. This gives cloud computing engineers
increased control over the communications occurring on your network.
Attraction 2: Glancing at the Building Blocks of Your Cloud Network
As a cloud administrator or cloud computing engineer, your ability to create a virtual network will typically be reliant on virtual machine software or a cloud network provided by a CSP. Virtual machine software allows cloud administrators to designate
and configure virtual network parameters associated with a host’s physical Network Interface Card (NIC). When you configure multiple hosts to operate using the same parameters, you are adding those hosts to the virtual network. Virtual networks
must have the following components:

- Virtual Switch
Virtual switches give you the capability to create segments on your network and connect those components together. You
can connect one or more virtual machines to a virtual switch. - Virtual Bridge
This component allows you to connect virtual machines to the LAN used
by the host computer. The virtual bridge connects the network adapter on the virtual machine to the physical NIC on the host computer. Multiple virtual bridges can be configured to connect to multiple physical NICs. - Virtual Host Adapter
The adapter makes it possible for your virtual machines to communicate with the host. Virtual host adapters are common in host-only and Network Address Translation (NAT) configurations. These cannot connect to an external network without a proxy server. - NAT Service
NAT services allow multiple devices within your cloud network to connect to the internet. - DHCP Server
The DHCP server allocates IP addresses to virtual machines and hosts. This applies to host-only and NAT configurations. - Ethernet Adapter
This is a physical network adapter installed on hosts that connect to the network.
Many CSPs provide cloud services that make it easier to configure virtual networks and cloud networks. With cloud networks, you configure your virtual network and add your resources to them, rather than configuring them at the virtual machine level. Cloud
networks also typically offer capabilities to simplify monitoring, management, connections and security.
Attraction 3: Surveying Network Configuration Options
If you want to make use of a virtual network, you must also configure the following components:
- Subnets
Subnets are a required part of a virtual network. You need TCP/IP subnets, which will designate addresses that are used on that network. Public and private address ranges are often used. When that’s not possible,
addresses are often assigned by CSPs. Virtual networks can be segmented into one or more subnets. - Routers or Routing Tables
For any network, you must configure routers or routing tables on any virtual machine connected to the network so that packets can be routed appropriately. - DNS
DNS server addresses must be provided, either assigned by you or your CSP. - CSP Region or Zones
Virtual networks operating in different CSP regions must be specified. Doing so will also allow you to connect virtual networks in different regions. If needed, you can configure isolation between regions
as well. - Traffic Filters
Configuring your traffic filters to the specifications of your security protocols will only allow approved traffic to pass through your network. Filters can be applied at NIC in virtual machines, to a subnet or
to a cloud service. When necessary, you will do this with a network virtual appliance.
Attraction 4: A Short Stop for Cloud Network Design Tips
When designing cloud networks, consider the following:
- As you design your cloud network, take the time to compare virtual network services offered by cloud providers. A hosted cloud network may be the only way you can create virtual networks the way you want them. Often, these cloud networks are easier
to configure and manage.
- If you plan to filter traffic (and most companies should!), plan testing of the filter into your deployment to avoid future user complaints due to blocked traffic.
- If you choose to go with a CSP, work with their personnel to configure your cloud network components, such as routing tables, network virtual appliances and subnets. Save yourself some hassle up front.
Attraction 5: Peek in to Prep Your Cloud Network’s Ports and Protocol
One of the key steps you need to take to secure your cloud network is drilling down into the nitty gritty to uncover what people, services and technologies need access to the network. Ports are an essential part of your cloud network. The port is the
endpoint of your connection.
Users connect to the cloud network through a designation port. All ports are assigned a number ranging from 0 to 65,535. The Internet Assigned Numbers Authority (IANA) separates port numbers into three ports, based on their numbers. TCP and UDP ports
are assigned based on these ranges. Hackers commonly go after well-known ports but have been known to target open registered or dynamic ports, as well.
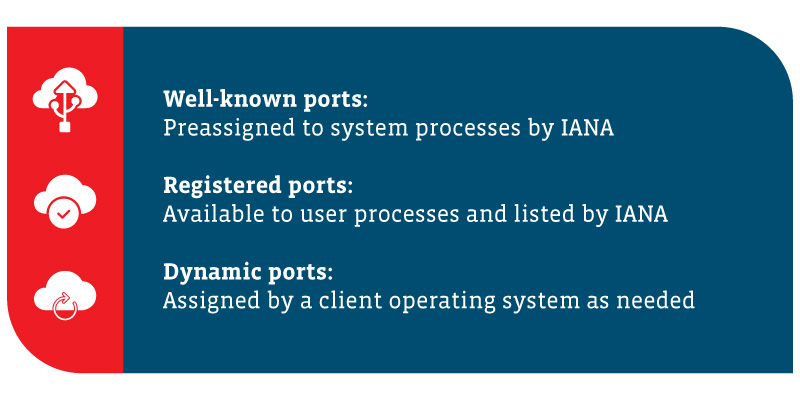
The three ports are:
- Well-known Ports
Preassigned to system processes by IANA, these include 0 to 1,023 and are most prone to attacks. - Registered Ports
Available to user processes and listed by IANA, these registered ports go from 1,024 to 49,15 and are known to be too system-specific for direct target by hackers. However, hackers sometimes scan for open ports
in this range. Don’t turn your back, but you can avert your gaze occasionally. - Dynamic or Private Ports
Assigned by a client operating system as needed, these are the ports numbered from 49,152 to 65,535. Dynamic ports are constantly changing (hence, the name dynamic), so it is difficult to directly target
numbers. But again, hackers have been known to scan for open ports. As far as watching for hackers is concerned, maybe you can turn your back on dynamic or private ports, but not for too long!
So, what are these ports used for? Here is a list of some of the most common default network ports used in the tech world:
- 21 FTP (File Transfer Protocol)
- 22 SSH (Secure Shell)
- 25 SMTP (Simple Mail Transfer Protocol)
- 53 DNS (Domain Name System)
- 80 HTTP (Hypertext Transfer Protocol)
- 110 POP3 (Post Office Protocol)
- 139 NetBIOS Session Service
- 143 IMAP (Internet Message Access Protocol)
- 443 HTTPS (Hypertext Transfer Protocol Secure)
- 3389 RDP (Remote Desktop Protocol)
Read more about ports and network protocols
Attraction 6: Seeing How You Can Service Your Cloud Network
Services and apps that float among the cloud are similar in many ways to the services and apps that remain grounded in your on-premises infrastructure. Take cloud-based web apps and directory services, for example. Many will use the same ports and protocols
that are used by their on-premise counterparts. Management tools, whether CSP-based, third-party or those built by your IT team, will also utilize port and protocol requirements.
If you decide to make the jump from the ground to the cloud, you will need to review your ports to determine what needs to be based in the cloud and what needs to remain housed on your own infrastructure. Take a close look at what needs internet access,
in order to communicate with outside services or apps, and what type of access is required from inside the cloud.
Once you narrow it down, you can configure firewalls and set the necessary filters to ensure your cloud network will remain secure. As you work to deploy your cloud network, make sure you consult the following resources:
- App and service configuration guides to identify the necessary ports and protocols each one uses.
- CSP security and deployment guides or white papers to locate the ports and protocols you need to access cloud services such as websites, databases, directory services and so on.
- Third-party deployment guides that are similar to the cloud network you are implementing.
- Your own (yes, your own) documentation to reference your firewall, routing, and other related information that could help you understand your own port and protocol usage. It will be tough to implement a successful cloud deployment if you have no idea from where you are jumping.
- If the fates forbid you from uncovering what ports and protocols are used by a legacy application that you want moved to the cloud, you might want to gather some helpful tools such as a port scanner or protocol analyzer to unlock the guarded secrets
of your predecessors.
Before launching any cloud network, take a fine-tooth comb through all your apps and services to ensure all ports and protocols are toeing the line.
Attraction 7: Determining Who Gets a Pass on the Cloud Network
Before you go giving those magic entry passes away and granting access to your cloud network, consider these guidelines in addition to the information already provided:
- Don’t assume you know all ports related to an app service. You know what assuming does, right? Don’t be on the receiving end of that.
- Pay close attention to the direction of traffic flow when you are creating inbound and outbound rules for network access.
Cloud networks are still an emerging technology, showing lots of possibility for the future of IT.

Attraction 8: An All-Access Pass with CompTIA Cloud+ Training and Certifications
If you see yourself moving into a cloud job like cloud specialist, cloud computing engineer or even data center manager, check out CompTIA Cloud+ to make sure you have the skills employers are looking for. CompTIA Cloud+ validates the skills and abilities
needed to implement and manage a successful cloud solution.
CompTIA Cloud+ is the only vendor-neutral, performance-based IT certification that views cloud computing as it relates to the broader ecosystem of IT operations.
This IT certification covers topics such as configuring and deploying cloud solutions and maintaining, managing and troubleshooting a secure cloud computing environment. The Official CompTIA Cloud+ Study Guide, and classes offered by CompTIA training partners, can help you get the knowledge you need for a successful career in cloud computing. Download the CompTIA Cloud+ exam objectives to see what’s on the exam, and purchase the study guide to begin your training.
Explore More Resources






