CompTIA Network+
Network+ certifies the essential skills needed to confidently design, configure, manage and troubleshoot wired and wireless networks.
Learn more Example questionsClick a career path and your experience level, and we'll show you the CompTIA certifications you need to get there!
Cybersecurity Professionals detect cyberthreats and implement changes to protect an organization. A security operations center (SOC) team likely has several tiers of cybersecurity professionals that are responsible for monitoring, directing, containing and remediating IT threats. Cybersecurity Professionals may be tasked with anything from installing, administering and troubleshooting security solutions to writing up security policies and training documents for colleagues. While other job roles are responsible for specific part of the overall system, Cybersecurity Professionals must be able to take a step back and see the big picture to keep it secure from threats.
| Experience Level | Beginner | Intermediate | Advanced |
|---|---|---|---|
| Annual salary range* | $61,520 – $102,600 | $79,400 – $131,340 | $102,600 – $165,920 |
| Job Postings* | 22250 | 66780 | 52140 |
| Number of certificates available at each level | 2 CompTIA Network+ CompTIA Security+ | 6 CompTIA CySA+ CompTIA PenTest+ CompTIA Project+ ISACA GIAC Cisco | 2 CompTIA CASP+ ISC2 CISSP |
| Experience Level | Beginner | Intermediate | Advanced |
|---|
Annual salary range*
$61,520 – $102,600
Job Postings*
Number of certificates available at each level
CompTIA Network+
CompTIA Security+
*CompTIA | Lightcast | U.S. Bureau of Labor Statistics
Note: Many employers don't specify any years of experience in job postings.
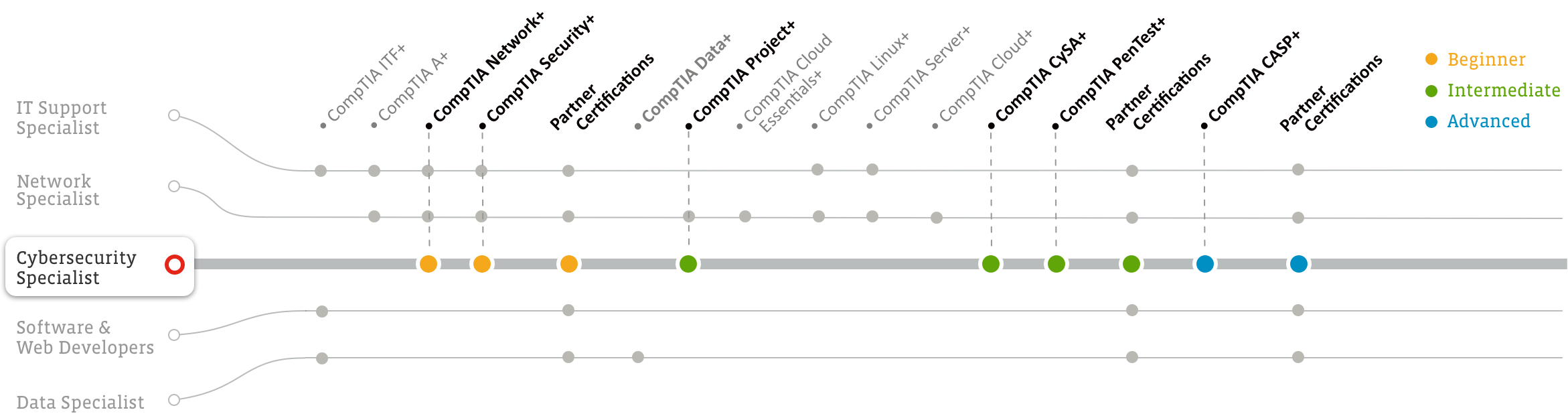
Certifications like ITF+, CompTIA A+ and Network+ give you the background you need if you don’t already have it, and CompTIA Security+ is recommended to begin your career as a Cybersecurity Professional.
Network+ certifies the essential skills needed to confidently design, configure, manage and troubleshoot wired and wireless networks.
Learn more Example questionsThe table below lists the domains measured by the full examination and the extent to which they are represented.
Domain and percentage of examination
| 1.0 Networking Concepts | 23% |
| 2.0 Infrastructure | 18% |
| 3.0 Network Operations | 17% |
| 4.0 Network Security | 20% |
| 5.0 Network Troubleshooting and Tools | 22% |
| Total | 100% |
Example Questions
An office workstation receives an Internet Protocol version 4 (IPv4) address from a Dynamic Host Configuration Protocol (DHCP) server. The IP lease includes the default gateway address which is the address of the office's layer 3 switch. A network administrator confirmed network connectivity by pinging the gateway. At what layer of the Open Systems Interconnection (OSI) are these two devices communicating with each other when using the ping command?
A. Layer 3 - Network B. Layer 2 - Data Link C. Layer 6 - Presentation D. Layer 7 - ApplicationA manager informs a support technician that users spend too much time using company computers for personal reasons. Which of the following can the technician implement to address the issue?
A. UTM appliance B. Layer 7 firewall C. Content filter D. Smart jackA network consultant is doing IT contingency planning and is trying to identify likely points of failure for the network. Which of the following would the consultant identify as Single Points of Failure in need of upgrades for added redundancy? (Select all that apply)
A. There is a lack of a load balancing device. B. A backup power generator is available on-site. C. There is a single power supply for a critical server. D. The main server is set up for full backup operations.An employee uses a key fob that contains a chip with a digital certificate and authenticates a person through a reader. Which of the following types of authentication factors does this describe?
A. Something you know B. Something you have C. Something you are D. Something you doA network administrator purchased new network switches from a vendor. Upon receiving and installing them, what should the admin do to harden the device to ensure secure device configuration of the switches? (Select all that apply)
A. Change default usernames and passwords. B. Remove vendor-installed backdoors. C. Disable or close unused ports and services. D. Implement a common prevalent password.A user installs a financial software package that requires cloud access. For some reason, the application fails to connect to the cloud server. What caused this issue?
A. Duplicate IP (Internet Protocol) address B. Incorrect host-based firewall settings C. Incorrect time D. Unresponsive serviceSecurity+ provides a global benchmark for best practices in IT network and operational security, one of the fastest-growing fields in IT.
Learn more Example questionsThe table below lists the domains measured by the full examination and the extent to which they are represented.
Domain and percentage of examination
| 1.0 Threats, Attacks and Vulnerabilities | 21% |
| 2.0 Technologies and Tools | 22% |
| 3.0 Architecture and Design | 15% |
| 4.0 Identity and Access Management | 16% |
| 5.0 Risk Management | 14% |
| 6.0 Cryptography and PKI | 12% |
| Total | 100% |
Example Questions
An attacker impersonates a member of the cleaning crew for a company's building, and requests an employee to hold the door open while the impersonator brings in a cleaning cart. The employee fell victim to what type of attack?
A. A lunchtime attack B. Shoulder surfing C. Piggy backing D. Dumpster divingThe DMZ (demilitarized zone) has a new virtual firewall server. A user reported that Internet websites are viewable, but no longer has a connection to an FTP (file transfer protocol) site. Which of the following is most likely the cause of the disconnection?
A. The user does not have access to the FTP site. B. A network cable disconnected from the server. C. The Firewall implicitly denied access to the FTP site. D. The ACL still requires setting up.A user has multiple documents to review, regarding a device from an authorized government vendor, with approval to use the documents. While attempting to send the documents to a personal email, to review later at home, the email returned with a message saying it failed to send. What is most likely the cause of this? (Select two)
A. Based on policy, the employee cannot use personal email. B. The DLP system flagged an incident. C. The antivirus software flagged the documents. D. The attachment file size is too large.After exploiting a vulnerability during testing, an administrator released a Security Update as a patch for Microsoft Internet Explorer. How should the administrator proceed in applying the patch?
A. Apply the patch directly to production. B. Apply the Security Update to the staging environment and test the system functionality. C. Wait for the quarterly update before patching the vulnerability. D. Apply the patch to the sandbox environment and test functionality.Fingerprint scanning is one of the most straightforward methods of biometric identification. Which of these concerns are most pertinent to the use of this technology?(Select two)
A. Ease of spoofing B. Surfaces must be clean and dry C. Revocability of credentials D. High expense of installationKey strength is based on length and randomness. One way to strengthen a key is to add a nonce or an Initialization Vector (IV). The same is true for passwords, which can be strengthened by adding a salt to a hashed password value. Evaluate the following to identify the statements that are true about nonces, IVs, and salts.(Select two)
A. The value of a nonce is hidden. B. A salt could be a counter value. C. Use of a salt ensures identical plaintexts produce different ciphertexts. D. Use of an initialization vector ensures identical plaintexts produce different ciphertexts.CompTIA offers everything you need to prepare for your certification exam. Explore training developed by CompTIA with options that fit various learning styles and timelines. Whether you prefer self-study or classroom training, CompTIA has you covered.